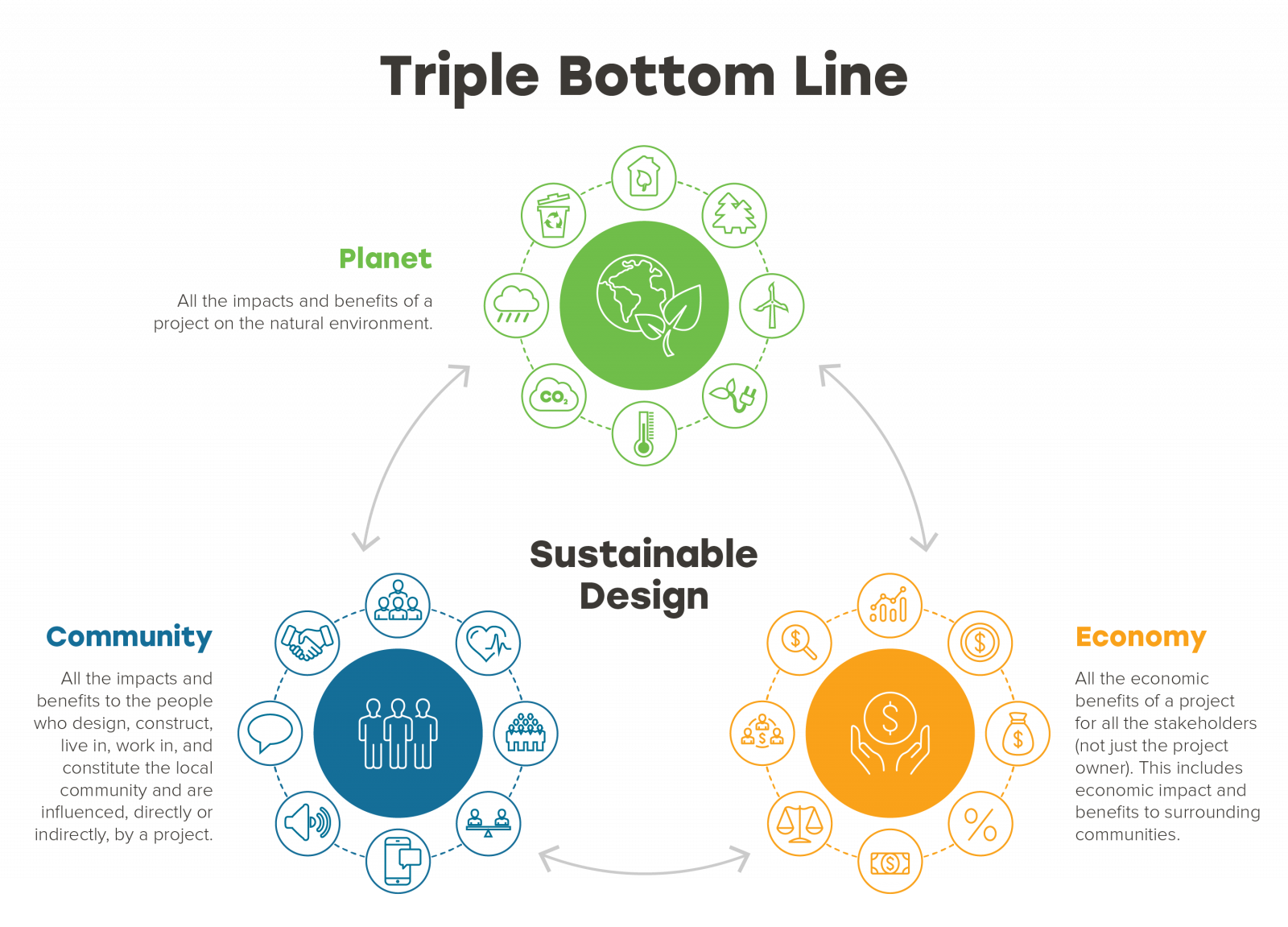
Ruth Lee Leaked

In today's digital age, where privacy and security are increasingly threatened, the recent Ruth Lee leak has sparked significant concern and raised important questions about data breaches and the potential impact on individuals and organizations.
This article aims to delve deep into the Ruth Lee leak, exploring its origins, the scope of the breach, the potential consequences, and the broader implications for data security. By examining this specific incident, we can gain valuable insights into the evolving landscape of cyber threats and the steps necessary to protect sensitive information.
Unveiling the Ruth Lee Leak: A Comprehensive Analysis

The Ruth Lee leak, which came to light in early 2023, has sent shockwaves through the online community. While the initial details were shrouded in mystery, further investigation has revealed a complex web of compromised data and potential fallout.
According to sources, the leak involved a substantial amount of sensitive information, including personal details, financial records, and confidential communications. The data breach is believed to have originated from a compromised database, likely the result of a sophisticated hacking attempt.
Scope of the Leak: Unraveling the Details
The scope of the Ruth Lee leak is vast and multifaceted. Initial reports indicate that the breach affected a wide range of individuals, from everyday internet users to high-profile figures in various industries. Here's a breakdown of the impacted categories:
- Individual Users: The leak exposed personal information of countless individuals, including names, addresses, phone numbers, and email addresses. This data, when in the wrong hands, can lead to identity theft, targeted phishing attacks, and other malicious activities.
- Financial Institutions: Financial records of multiple banks and investment firms were compromised, raising concerns about potential fraud and unauthorized access to sensitive financial data. The impact on these institutions could be severe, affecting their reputation and customer trust.
- Corporate Entities: Numerous businesses, across diverse sectors, were affected by the leak. This includes confidential business plans, trade secrets, and customer data. The leak has the potential to disrupt operations, cause financial losses, and damage the competitive advantage of these organizations.
- Public Figures: High-profile individuals, such as celebrities, politicians, and influential personalities, had their private communications and personal details exposed. This not only poses a risk to their personal safety but also has the potential to influence public perception and political dynamics.
The diversity of affected entities highlights the far-reaching implications of the Ruth Lee leak, making it a critical case study for understanding the impact of data breaches.
Technical Analysis: How the Leak Occurred
Investigations into the Ruth Lee leak have revealed a sophisticated hacking operation, utilizing advanced techniques to infiltrate and exfiltrate data. The attackers, believed to be a well-organized cybercriminal group, exploited vulnerabilities in the targeted systems to gain unauthorized access.
One of the key factors in the success of the attack was the use of a zero-day exploit, a previously unknown vulnerability in the targeted software. This allowed the hackers to bypass security measures and gain control over critical systems. The exploit was later identified as a remote code execution vulnerability, enabling the attackers to execute arbitrary code and manipulate the system to their advantage.
| Attack Vector | Description |
|---|---|
| Phishing Emails | The hackers sent carefully crafted phishing emails to employees of the targeted organizations, tricking them into providing login credentials and other sensitive information. |
| Malware Infection | By exploiting vulnerabilities in commonly used software, the attackers were able to install malware on target systems, providing a backdoor for future access. |
| Man-in-the-Middle Attacks | In some cases, the hackers intercepted communications between users and servers, allowing them to steal credentials and sensitive data in transit. |

The technical sophistication of the attack highlights the need for continuous security updates, robust cybersecurity measures, and employee education to mitigate the risk of such breaches.
Impact and Implications: Navigating the Aftermath
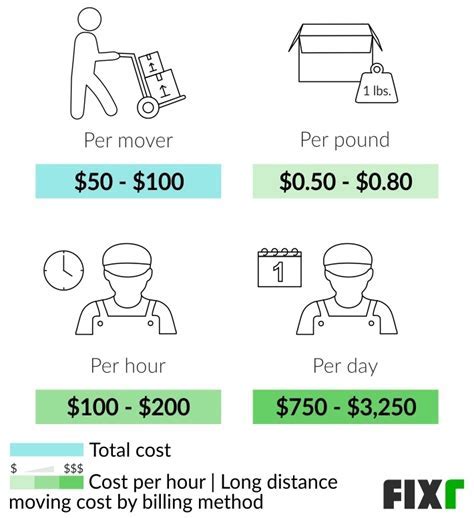
The Ruth Lee leak has had far-reaching consequences, affecting not only the individuals and organizations directly involved but also raising broader concerns about data security and privacy.
Immediate Impact on Affected Entities
For the individuals whose personal information was exposed, the leak has led to a range of immediate consequences. Many have reported increased spam and phishing attempts, as well as concerns about identity theft and financial fraud. The emotional toll of such breaches, including anxiety and a sense of violation, cannot be overlooked.
Similarly, the affected organizations are facing significant challenges. Financial institutions are working tirelessly to mitigate the risk of fraud and protect their customers' assets. Corporate entities are assessing the potential impact on their operations, intellectual property, and customer relationships. Public figures and celebrities are grappling with the potential damage to their public image and personal safety.
Long-Term Implications for Data Security
Beyond the immediate fallout, the Ruth Lee leak has significant implications for the future of data security. It serves as a stark reminder of the ever-present threat of cyberattacks and the need for proactive measures to protect sensitive information.
One key takeaway is the importance of robust cybersecurity practices. Organizations must invest in advanced security solutions, regular vulnerability assessments, and employee training to minimize the risk of similar breaches. The leak also highlights the need for better data protection regulations and international collaboration to combat cybercrime effectively.
Furthermore, the incident underscores the critical role of user awareness and education. Individuals must be vigilant about their online activities, recognizing potential threats and taking steps to protect their personal information. This includes using strong passwords, enabling two-factor authentication, and being cautious of suspicious emails or websites.
Conclusion: Learning from the Ruth Lee Leak
The Ruth Lee leak serves as a sobering reminder of the fragility of our digital world and the constant threat posed by cybercriminals. While the immediate impact of the breach is devastating, it also presents an opportunity to learn and improve our data security practices.
By understanding the scope, technical intricacies, and implications of the leak, we can work towards a more secure digital environment. This includes investing in robust cybersecurity measures, fostering international collaboration, and empowering individuals with the knowledge to protect their digital lives.
As we navigate the aftermath of the Ruth Lee leak, let us embrace the lessons learned and take proactive steps to safeguard our sensitive information. Together, we can build a more resilient digital ecosystem, minimizing the risk of future breaches and protecting the privacy and security of individuals and organizations alike.
What can individuals do to protect their data in the wake of a leak like Ruth Lee?
+Individuals can take several proactive steps to enhance their data security. This includes regularly updating passwords, enabling two-factor authentication, and being cautious of suspicious emails or websites. It’s also crucial to monitor financial accounts and credit reports for any signs of fraud or unauthorized activity.
How can organizations improve their cybersecurity measures to prevent future breaches?
+Organizations should prioritize cybersecurity by investing in advanced security solutions, conducting regular vulnerability assessments, and providing comprehensive employee training. Additionally, they should consider implementing multi-factor authentication, data encryption, and access control measures to enhance their security posture.
What are the legal consequences for the perpetrators of data breaches like the Ruth Lee leak?
+The legal consequences for data breaches can vary depending on the jurisdiction and the specific laws in place. In many cases, perpetrators can face criminal charges, fines, and civil lawsuits. Additionally, they may be subject to regulatory penalties and public scrutiny, which can have severe reputational and financial impacts.