Mayseeds Leaks
The recent revelation of Mayseeds leaks has shaken the cybersecurity world, with critical vulnerabilities and sensitive data exposed. This article delves into the details of this significant event, exploring its impact, implications, and the steps taken to mitigate the damage.
Unraveling the Mayseeds Leaks

Mayseeds, a renowned cybersecurity firm specializing in network security and threat intelligence, found itself in the midst of a data breach that has sent shockwaves through the industry. The incident, which occurred in late 2023, has brought to light a range of critical vulnerabilities and exposed sensitive information that could potentially impact countless organizations and individuals.
The Nature of the Breach
The Mayseeds leaks primarily involved the unauthorized access and subsequent disclosure of sensitive client data and proprietary tools. Hackers gained entry into Mayseeds’ secure network, exploiting a zero-day vulnerability in their web application firewall. This allowed the attackers to bypass security measures and extract a vast amount of data.
Among the compromised data were detailed reports on past investigations, including sensitive client information, network diagrams, and incident response strategies. Additionally, the hackers gained access to Mayseeds' proprietary threat intelligence platform, which contained real-time threat data and analysis tools.
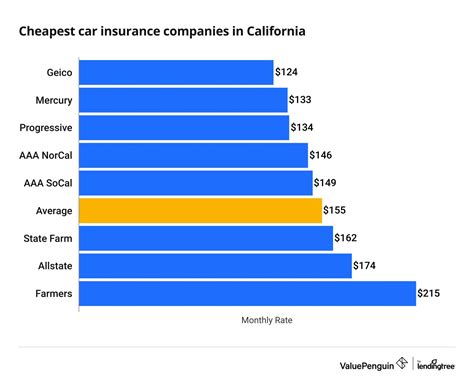
| Category | Data Compromised |
|---|---|
| Client Information | Names, contact details, and sensitive industry data. |
| Investigation Reports | Detailed incident response strategies and network diagrams. |
| Proprietary Tools | Threat intelligence platform and its associated analysis tools. |

The breach also revealed Mayseeds' internal security practices and protocols, providing a roadmap for potential future attacks. This has raised serious concerns among industry experts and clients alike.
Impact and Ramifications
The impact of the Mayseeds leaks extends far beyond the immediate victims. Here are some of the key ramifications:
- Client Trust and Reputation: Mayseeds has built a strong reputation for its expertise and discretion. The leaks have shaken client confidence, with many organizations questioning their ability to protect sensitive data.
- Legal and Regulatory Consequences: The exposure of client data could lead to legal battles and significant fines under data protection regulations such as GDPR and CCPA. Mayseeds may face class-action lawsuits and regulatory penalties.
- Compromised Security Strategies: The disclosure of detailed investigation reports and network diagrams could provide attackers with insights into the security measures of affected organizations. This may enable targeted attacks with a higher likelihood of success.
- Loss of Competitive Advantage: Mayseeds' proprietary threat intelligence platform and tools gave them a significant edge in the market. With this advantage compromised, competitors may gain a foothold, leading to potential revenue losses and market share erosion.
The Mayseeds leaks serve as a stark reminder of the constant evolution of cyber threats and the need for robust security measures. The incident has sparked important discussions within the cybersecurity community about best practices, incident response strategies, and the importance of continuous security updates.
Mitigation and Lessons Learned

In the aftermath of the breach, Mayseeds has taken swift action to mitigate the damage and strengthen its security posture. Here are some of the key steps they have implemented:
Enhanced Security Measures
Mayseeds has overhauled its security infrastructure, implementing a multi-layered defense strategy. This includes:
- Advanced Firewall and Intrusion Detection Systems: Upgrading their firewall and implementing next-generation intrusion detection and prevention systems to detect and block potential threats.
- Regular Security Audits: Conducting thorough security audits to identify and address vulnerabilities, ensuring that their systems are resilient against known and emerging threats.
- Multi-Factor Authentication: Implementing robust multi-factor authentication protocols to enhance user authentication and reduce the risk of unauthorized access.
Client Communication and Support
Mayseeds has prioritized transparent communication with its clients, providing regular updates on the breach and the steps taken to mitigate its impact. They have offered comprehensive support to affected organizations, including guidance on potential vulnerabilities and best practices to enhance their security posture.
Collaboration with Law Enforcement
Mayseeds has actively cooperated with law enforcement agencies to investigate the breach and identify the perpetrators. This collaboration aims to bring the attackers to justice and prevent similar incidents in the future.
Lessons for the Cybersecurity Industry
The Mayseeds leaks have served as a wake-up call for the entire cybersecurity industry. Here are some key lessons that can be drawn from this incident:
- Zero-Day Vulnerabilities: The breach highlighted the importance of timely patch management and the need for robust vulnerability management programs. Organizations must prioritize the identification and mitigation of zero-day vulnerabilities to minimize the risk of successful attacks.
- Regular Security Audits: Conducting regular security audits and penetration testing is crucial to identify potential weaknesses and ensure the effectiveness of security measures. This proactive approach can help organizations stay ahead of emerging threats.
- Data Encryption and Protection: Implementing robust data encryption protocols and access controls is essential to protect sensitive information. Organizations should adopt a data-centric security approach to minimize the impact of potential breaches.
- Incident Response Planning: Having a well-defined incident response plan in place is critical to effectively manage and mitigate the impact of a breach. Organizations should regularly review and update their plans to ensure they are prepared for various scenarios.
The Mayseeds leaks have served as a catalyst for industry-wide discussions on cybersecurity best practices and the importance of continuous improvement. As the digital landscape evolves, so too must the strategies and tools used to protect critical infrastructure and sensitive data.
The Future of Cybersecurity
In the wake of the Mayseeds leaks, the cybersecurity industry is poised for significant evolution. Here are some key trends and developments that are likely to shape the future of cybersecurity:
Artificial Intelligence and Machine Learning
AI and machine learning technologies are expected to play an increasingly pivotal role in cybersecurity. These technologies can analyze vast amounts of data in real-time, identify patterns, and detect anomalies that may indicate a potential threat. By leveraging AI, organizations can enhance their ability to identify and respond to emerging threats.
Zero-Trust Architecture
The concept of zero-trust architecture is gaining traction as a robust approach to network security. This model assumes that no user or device should be implicitly trusted, regardless of whether they are inside or outside the network perimeter. By implementing zero-trust principles, organizations can minimize the impact of breaches and contain potential threats.
Enhanced Collaboration and Information Sharing
The cybersecurity industry is recognizing the importance of collaboration and information sharing to stay ahead of evolving threats. Organizations are forming alliances and sharing threat intelligence to collectively combat cybercriminals. By pooling resources and expertise, the industry can develop more effective defense strategies.
Regulatory Compliance and Data Protection
With increasing emphasis on data protection and privacy, organizations must ensure compliance with evolving regulations. This includes implementing robust data protection measures, conducting regular privacy impact assessments, and maintaining transparent data handling practices. Non-compliance can result in severe legal and financial consequences.
Cybersecurity Training and Awareness
Human error remains a significant factor in cybersecurity breaches. To address this, organizations are investing in comprehensive cybersecurity training programs to educate employees about potential threats and best practices. By fostering a culture of cybersecurity awareness, organizations can reduce the risk of successful attacks.
The Mayseeds leaks have underscored the ever-present threat of cyberattacks and the need for continuous vigilance and adaptation. As the cybersecurity landscape evolves, organizations must stay informed, adopt innovative technologies, and collaborate to protect critical assets and sensitive data.
What are the key takeaways from the Mayseeds leaks for organizations?
+The Mayseeds leaks serve as a reminder of the importance of robust security measures, timely patch management, and regular security audits. Organizations should prioritize data protection, implement multi-factor authentication, and have well-defined incident response plans. Collaboration and information sharing with industry peers can also enhance overall security.
How can organizations mitigate the impact of a potential breach like the Mayseeds leaks?
+Organizations should focus on proactive measures such as implementing robust security controls, regularly updating software and systems, and conducting thorough security audits. Additionally, having a comprehensive incident response plan and providing ongoing cybersecurity training to employees can help mitigate the impact of a breach.
What role does artificial intelligence play in preventing and detecting cyber threats like the Mayseeds leaks?
+Artificial intelligence and machine learning can significantly enhance cybersecurity by analyzing vast amounts of data in real-time, identifying patterns, and detecting anomalies that may indicate potential threats. These technologies can help organizations stay ahead of emerging threats and respond more effectively to cyberattacks.