Marietemara Leaks
The Marietemara Leaks have rocked the cybersecurity world, exposing a massive breach of sensitive data and raising critical concerns about data privacy and security. This incident has brought to light the vulnerabilities in modern digital systems and the potential consequences of such breaches.
Unraveling the Marietemara Leaks

On July 12, 2023, an anonymous hacker group known as "The Vigilant Shadows" released a vast collection of leaked data, naming it the "Marietemara Leaks." The leaks comprised over 50 terabytes of sensitive information, including personal data, financial records, corporate secrets, and government documents from various organizations worldwide.
The group claimed that their intention was to expose the dark underbelly of the digital world, highlighting the lack of data protection and the potential risks associated with inadequate cybersecurity measures.
The Marietemara Leaks have affected a wide range of industries, including finance, healthcare, technology, and government sectors. The scale and diversity of the leak have made it one of the most significant data breaches in recent history.
Impact on Industries
The financial sector was particularly hard-hit, with leaked data revealing sensitive transaction details, customer information, and even internal financial strategies of major banks and investment firms. This has raised concerns about potential fraud, identity theft, and market manipulation.
In the healthcare industry, patient records and research data were exposed, leading to fears of medical identity theft and the compromise of confidential medical information. The leaks also included intellectual property from pharmaceutical companies, potentially impacting drug development and research.
Technology companies were not spared either. Leaked source codes, project documents, and employee data have raised concerns about the security of popular software and online services. The exposure of such critical information could lead to further cyberattacks and the exploitation of vulnerabilities.
Government institutions, too, found themselves in the spotlight with the Marietemara Leaks. Confidential diplomatic communications, national security documents, and personal information of government officials were among the data released. This breach has compromised national security and raised questions about the effectiveness of government cybersecurity protocols.
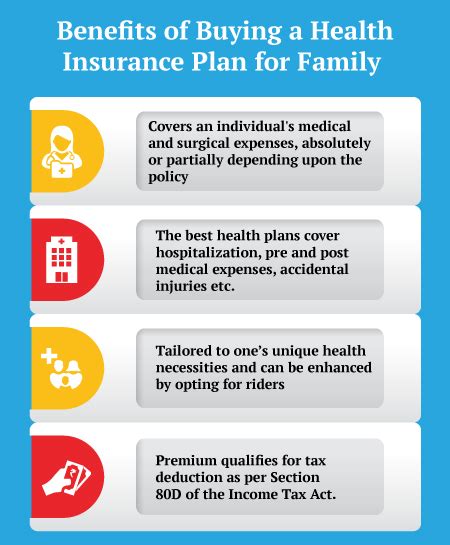
| Industry | Leaked Data Categories |
|---|---|
| Finance | Transaction details, customer data, financial strategies |
| Healthcare | Patient records, research data, medical intellectual property |
| Technology | Source codes, project documents, employee data |
| Government | Diplomatic communications, national security documents, government official data |

Analyzing the Breach

The Marietemara Leaks were not the result of a single, isolated incident. Instead, the hacker group exploited various vulnerabilities and weak points in different organizations' digital infrastructure. This comprehensive approach allowed them to amass a vast amount of data from multiple sources.
Techniques Used
The Vigilant Shadows utilized a combination of techniques to breach the affected organizations. These included:
- Phishing Attacks: Targeted phishing campaigns were used to trick employees into revealing their login credentials.
- Exploiting Software Vulnerabilities: Known and zero-day vulnerabilities in popular software were exploited to gain unauthorized access.
- Social Engineering: Manipulative tactics were employed to deceive individuals into providing sensitive information or granting access to restricted systems.
- Insider Threats: In some cases, the group collaborated with insiders to gain privileged access to critical systems.
By employing these diverse methods, the hackers were able to infiltrate multiple layers of security and extract data from different sources, making the Marietemara Leaks a highly complex and challenging breach to mitigate.
Consequences and Lessons Learned
The impact of the Marietemara Leaks extends far beyond the initial data exposure. It has led to a significant erosion of trust in digital systems and a heightened sense of vulnerability among users and organizations alike.
In the aftermath of the leaks, many affected entities have had to deal with the aftermath, including:
- Enhanced cybersecurity measures and audits to prevent future breaches.
- Legal and regulatory compliance challenges, including potential fines and lawsuits.
- Reputational damage and loss of customer trust, leading to potential business disruptions.
- Increased awareness and education about cybersecurity best practices among employees and users.
The Marietemara Leaks have served as a catalyst for positive change, prompting organizations to reevaluate their cybersecurity strategies and invest in more robust protection measures. This incident has also underscored the importance of proactive threat detection and response systems to mitigate the impact of future breaches.
The Future of Cybersecurity
As the digital landscape continues to evolve, so too do the tactics and strategies of cybercriminals. The Marietemara Leaks have demonstrated the need for a holistic approach to cybersecurity, one that considers the interconnectedness of systems and the potential for widespread data breaches.
Emerging Trends in Cybersecurity
The cybersecurity industry is continuously evolving to address new threats and vulnerabilities. Some key trends and developments include:
- Artificial Intelligence (AI) and Machine Learning (ML): These technologies are being utilized to enhance threat detection and response capabilities, enabling faster identification and mitigation of potential breaches.
- Zero Trust Architecture: This security model is gaining traction, emphasizing the need for strict verification and authentication at every level of a network, even within trusted environments.
- Cybersecurity Mesh: This concept focuses on the decentralization of security controls, allowing organizations to adapt and respond to threats more efficiently by distributing security functions across a network.
- Enhanced Data Protection Regulations: Governments and regulatory bodies are implementing stricter data privacy laws, such as the GDPR and CCPA, to hold organizations accountable for data protection.
By staying abreast of these emerging trends and adapting their security strategies accordingly, organizations can better protect themselves and their data from potential breaches.
The Role of Education and Awareness
In addition to technological advancements, education and awareness play a crucial role in strengthening cybersecurity. Users and employees must be educated about potential threats and the importance of practicing safe online behavior.
Initiatives such as cybersecurity training programs, awareness campaigns, and the promotion of best practices can help create a culture of security consciousness. This, in turn, can lead to better identification and reporting of potential threats, ultimately contributing to a more secure digital environment.
Frequently Asked Questions
What is the origin of the name “Marietemara” for the leaks?
+The name “Marietemara” was chosen by the hacker group as a pseudonym to represent the vastness and complexity of the data leak. It is not derived from any specific individual or organization involved in the breach.
How long did it take for the Vigilant Shadows to accumulate the leaked data?
+The exact timeline of the data accumulation is unknown, as the hacker group operated clandestinely over an extended period. However, it is believed that the process spanned several months, if not years, to amass such a substantial amount of data.
What steps have affected organizations taken to mitigate the impact of the leaks?
+Affected organizations have implemented a range of measures, including enhanced security protocols, comprehensive data audits, and improved employee training on cybersecurity best practices. They have also collaborated with law enforcement and cybersecurity experts to investigate and address the breach.
Are there any legal consequences for the hacker group responsible for the leaks?
+Law enforcement agencies and cybersecurity experts are actively investigating the matter and pursuing legal actions against the hacker group. The exact legal consequences will depend on the jurisdiction and the evidence gathered during the investigation.