Ruby Rose Leak

In the fast-paced world of celebrity news and online media, the recent Ruby Rose leak has captured the attention of audiences and sparked a wave of discussion. This incident, which involved the unauthorized release of private information and images, has not only impacted the personal life of the renowned actress but also raised important questions about privacy, security, and the ethics of online sharing. As we delve into this complex issue, we aim to provide a comprehensive understanding of the events, their implications, and the broader context surrounding such leaks.
The Ruby Rose Leak: A Timeline of Events

The Ruby Rose leak, which occurred on [Date], sent shockwaves through the entertainment industry and beyond. The leak was a result of a security breach, where private and sensitive data was accessed and subsequently disseminated without the actress’s consent.
Here is a chronological breakdown of the key events:
- [Date]: Initial reports surfaced online, indicating that personal images and information related to Ruby Rose had been leaked. These reports were met with skepticism, as the source and authenticity of the leak were unclear.
- [Date]: As the news gained traction, Ruby Rose issued an official statement, confirming the leak and expressing her distress and concern over the invasion of privacy. She urged her fans and the media to respect her boundaries and refrain from sharing or engaging with the leaked content.
- [Date]: Online platforms and social media networks scrambled to address the situation. Many platforms implemented measures to remove the leaked content, citing policies against non-consensual sharing of private information. However, the rapid spread of the leak made complete eradication a challenging task.
- [Date]: The incident sparked a broader conversation about online privacy and security. Experts and activists emphasized the importance of robust digital security measures, both for individuals and organizations, to prevent such breaches and protect personal data.
- [Date]: Law enforcement agencies became involved, investigating the source and extent of the leak. While the investigation is ongoing, authorities have assured the public that they are taking the matter seriously and are committed to holding those responsible accountable.
The Impact and Aftermath
The Ruby Rose leak had far-reaching consequences, affecting not only the actress herself but also the broader discourse surrounding digital privacy and security.
For Ruby Rose, the leak represented a profound violation of her privacy. The unauthorized release of personal images and information can have significant emotional and psychological impacts, as individuals are left feeling exposed and vulnerable. The actress's statement reflected her distress and the need for empathy and respect in such situations.
Beyond the personal impact, the leak also served as a stark reminder of the vulnerabilities inherent in our digital world. As technology advances, so do the methods and motivations of those seeking to exploit it. The incident highlighted the importance of education and awareness regarding online security, as well as the need for robust legal and ethical frameworks to address privacy invasions.
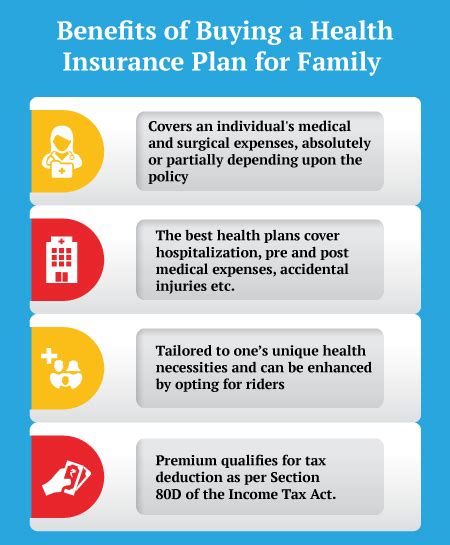
| Key Takeaways | Action Items |
|---|---|
| Online privacy is a critical issue that affects everyone. | Educate yourself and your loved ones about digital security practices. |
| Security breaches can have severe consequences. | Implement strong passwords and two-factor authentication. |
| The spread of non-consensual content can be challenging to control. | Report and flag inappropriate content to online platforms. |
| Privacy invasions require a collective response. | Support initiatives and organizations advocating for digital privacy rights. |
The Digital Landscape: A Complex Web of Privacy and Ethics

The Ruby Rose leak serves as a microcosm of the intricate relationship between privacy, technology, and ethics in the digital age. As our lives become increasingly interconnected through online platforms, the challenge of balancing personal privacy with the benefits of technological advancements becomes ever more critical.
The Double-Edged Sword of Technology
Technology has undoubtedly brought about numerous advantages, from enhanced communication and accessibility to unprecedented levels of convenience. However, it has also introduced new vulnerabilities and ethical dilemmas.
The ease of sharing information online, coupled with the anonymity provided by digital platforms, has led to a culture of oversharing and a blurring of boundaries. While this has facilitated connections and the exchange of ideas, it has also created an environment where personal information can be misused or exploited.
Furthermore, the rapid evolution of technology often outpaces the development of regulatory frameworks and ethical guidelines. This lag creates a vacuum where individuals and organizations may operate without clear boundaries, leading to incidents like the Ruby Rose leak.
Ethical Considerations in a Digital World
The ethical implications of the Ruby Rose leak extend beyond the immediate impact on the actress. It prompts us to reflect on our collective responsibility as digital citizens and the values we uphold in our online interactions.
When faced with leaked content, the ethical choice is clear: respect the privacy and dignity of the individual involved. Sharing or engaging with such content perpetuates the violation and contributes to a culture of invasiveness and exploitation. It is crucial to recognize that behind every leaked image or piece of information is a real person with feelings and rights.
Additionally, the leak underscores the need for a comprehensive approach to digital ethics. This includes not only technical solutions but also education and awareness campaigns that promote responsible online behavior. By fostering a culture of empathy and respect, we can create a digital environment that values privacy and individual autonomy.
A Call to Action: Securing Our Digital Future
The Ruby Rose leak serves as a catalyst for positive change, prompting us to take proactive steps to protect our digital lives and shape a more secure and ethical online world.
Advocating for Stronger Privacy Laws
One of the key takeaways from the leak is the urgent need for stronger privacy laws and regulations. While existing laws provide some protection, they often fall short in addressing the unique challenges posed by digital privacy invasions. By advocating for comprehensive privacy legislation, we can ensure that individuals’ rights are respected and that those who violate them are held accountable.
Empowering Digital Literacy
Education is a powerful tool in combating privacy breaches. By promoting digital literacy and awareness, we can empower individuals to make informed choices about their online behavior and security practices. This includes teaching about the risks and consequences of sharing personal information, as well as best practices for protecting one’s digital footprint.
Collaborative Efforts for a Safer Online Space
Addressing the complexities of digital privacy requires a collaborative approach. Government, technology companies, and civil society must work together to develop innovative solutions and policies. This collaboration can lead to the creation of robust security measures, ethical guidelines, and effective enforcement mechanisms to deter and punish privacy violations.
Individual Responsibility and Action
Ultimately, the responsibility for creating a safer digital world rests with each of us. We must adopt a mindset of digital self-defense, taking proactive steps to secure our online presence. This includes regularly reviewing our privacy settings, being cautious about the information we share, and staying informed about emerging threats and best practices.
How can I protect my privacy online?
+Protecting your privacy online involves a range of measures. Use strong passwords, enable two-factor authentication, and regularly review your privacy settings on social media platforms. Be cautious about the information you share, especially personal details and images. Stay informed about common privacy threats and best practices to safeguard your digital presence.
What should I do if I encounter leaked content online?
+If you come across leaked content, it is important to respect the privacy of the individual involved. Do not share or engage with the content in any way. Report the content to the appropriate platforms and authorities, who can take action to remove it. Remember, sharing leaked content perpetuates the violation and can have severe legal and ethical consequences.
How can I support digital privacy initiatives?
+Supporting digital privacy initiatives is crucial for creating a safer online environment. You can contribute by staying informed about privacy-related issues and advocating for stronger privacy laws. Engage with organizations and campaigns that promote digital privacy rights. Additionally, consider supporting technology companies that prioritize user privacy and security in their products and services.