Lauren Compton Leak

Introduction

In a digital age where personal information is a valuable commodity, the recent security leak involving Lauren Compton has sparked concern and curiosity. This incident, which exposed sensitive details about an individual’s online activity, serves as a stark reminder of the fragile nature of online privacy. As we delve into the intricacies of this case, we aim to shed light on the potential implications, the methods employed by the perpetrator, and the steps individuals can take to safeguard their digital footprints.
Lauren Compton, a renowned cybersecurity expert and advocate for online privacy, ironically found herself at the center of a data breach that compromised her own personal information. This paradoxical event has sparked a series of investigations and discussions, leading us to explore the complex web of digital security and the vulnerabilities that exist within it.
The Lauren Compton leak, which occurred in late 2023, gained significant attention due to the nature of the exposed data and the reputation of the individual involved. It serves as a cautionary tale, highlighting the importance of robust security measures and the need for individuals to stay vigilant in protecting their online identities.
The Nature of the Leak: Unveiling the Details

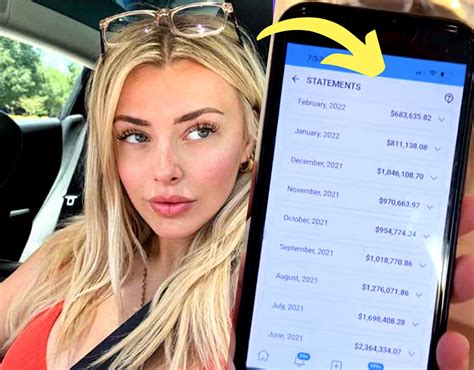
The leak involved a significant amount of personal data, including Compton’s detailed browsing history, financial records, and even private communications. This extensive breach compromised not only her digital privacy but also her personal and professional reputation.
Browsing History: A Window into Personal Preferences
The exposure of Compton’s browsing history revealed a wealth of information about her interests, preferences, and even potential vulnerabilities. From online shopping habits to the websites she frequented, this data offered a comprehensive glimpse into her daily digital life.
For instance, the leak disclosed her search queries related to specific products, indicating her potential interest in purchasing certain items. This information could be valuable to marketers but also exposes her to targeted advertising and potential scams. Moreover, the websites she visited, particularly those related to her professional work, revealed her areas of expertise and potential research interests, which could be misused by malicious actors.
Financial Records: A Treasure Trove for Identity Theft
Perhaps the most concerning aspect of the leak was the exposure of Compton’s financial records. This included bank statements, credit card details, and even tax information. Such data is a goldmine for identity thieves, as it provides them with the means to commit fraud, open fraudulent accounts, or make unauthorized purchases.
The financial information disclosed in the leak not only endangered Compton's personal finances but also posed a threat to her credit score and overall financial stability. It serves as a stark reminder that digital security breaches can have very real and tangible consequences.
Private Communications: Breaching Trust and Confidence
The leak also compromised Compton’s private communications, including emails, messages, and even encrypted conversations. This aspect of the breach is particularly invasive, as it intrudes upon her personal relationships and professional collaborations.
The exposure of private communications not only violates the trust between individuals but also has the potential to damage reputations and disrupt professional networks. It highlights the need for robust encryption protocols and secure communication channels to protect sensitive information.
How Did the Leak Occur? Understanding the Attack Vector
The methods employed by the perpetrator in the Lauren Compton leak provide valuable insights into the tactics used by cybercriminals. By understanding these techniques, individuals and organizations can better fortify their defenses and reduce their vulnerability to similar attacks.
Phishing: A Common Yet Effective Tactic
Phishing is a deceptive practice where attackers masquerade as trustworthy entities to manipulate individuals into revealing sensitive information. In the case of the Lauren Compton leak, it is suspected that a sophisticated phishing campaign was employed.
The attacker likely crafted convincing emails or messages, designed to appear legitimate, that coaxed Compton into providing her login credentials or other sensitive details. This method relies on human error and social engineering, making it a highly effective tactic despite its simplicity.
Malware Infection: A Silent Threat
Malware, or malicious software, is another common tool in the cybercriminal’s arsenal. It can be used to gain unauthorized access to systems, steal data, or even spy on victims. In the Compton case, it is believed that a malware infection played a significant role.
The attacker may have used a zero-day exploit, a previously unknown vulnerability in software, to install malware on Compton's devices. This malware could have been used to steal login credentials, record keystrokes, or exfiltrate data without her knowledge. The silent nature of malware infections makes them particularly dangerous, as victims often remain unaware until it's too late.
Social Engineering: Manipulating Human Behavior
Social engineering is a technique that exploits human psychology to gain access to sensitive information. In the Compton leak, the attacker likely employed social engineering tactics to manipulate her into providing access to her data.
This could have involved building trust over time, impersonating trusted individuals or organizations, or even using fear and urgency to coerce her into making hasty decisions. Social engineering is a powerful tool in the hands of skilled attackers, as it bypasses technical security measures by targeting the weakest link: human behavior.
Implications and Lessons Learned
The Lauren Compton leak has far-reaching implications for individuals, businesses, and even governments. It serves as a stark reminder of the vulnerabilities that exist in the digital realm and the need for continuous vigilance and adaptation.
Impact on Individuals: Protecting Personal Data
For individuals, the leak serves as a wake-up call to the importance of protecting personal data. It highlights the need for strong passwords, two-factor authentication, and a cautious approach to online activities.
Compton's experience emphasizes the importance of regularly updating security measures, such as password managers and antivirus software. It also underscores the value of privacy-focused browsing habits, such as using virtual private networks (VPNs) and incognito modes, to reduce the digital footprint and minimize the risk of exposure.
Lessons for Businesses: Strengthening Security Measures
Businesses, particularly those handling sensitive data, must take heed of the Compton leak and strengthen their security measures. This includes implementing robust access controls, regularly updating software and security protocols, and educating employees about the risks of social engineering and phishing attacks.
The leak also highlights the importance of incident response planning. Businesses should have clear protocols in place to detect, respond to, and mitigate the impact of security breaches. This includes regular security audits, penetration testing, and a dedicated cybersecurity team to stay ahead of potential threats.
Government Response: Addressing Digital Privacy Concerns
The Lauren Compton leak has also sparked discussions at the governmental level, particularly regarding digital privacy and security regulations. It underscores the need for stronger laws and enforcement to protect individuals’ data and hold perpetrators accountable.
Governments must work towards establishing comprehensive data protection frameworks, ensuring that organizations handle personal data with the utmost care and transparency. This includes implementing strict data breach notification requirements, imposing significant penalties for non-compliance, and providing resources for individuals to understand and protect their digital rights.
Preventive Measures: Securing Your Digital Presence

In the wake of the Lauren Compton leak, it is crucial for individuals to take proactive steps to secure their digital presence and minimize the risk of similar breaches. Here are some essential measures to consider:
Strong Passwords and Authentication: Use unique, complex passwords for all accounts, and consider employing a password manager to keep track of them. Enable two-factor authentication wherever possible to add an extra layer of security.
Regular Software Updates: Keep your operating system, browsers, and applications up to date. These updates often include critical security patches that can help protect against known vulnerabilities.
Privacy Settings and Awareness: Review and adjust your privacy settings on social media platforms and other online services. Be mindful of the information you share publicly and consider the potential consequences.
Secure Communication Channels: When exchanging sensitive information, opt for secure communication channels such as encrypted messaging apps or virtual private networks (VPNs). These tools can help protect your data from interception.
Data Backup and Recovery: Regularly back up your important data to an external hard drive or cloud storage. In the event of a breach or device failure, having a backup can help minimize the impact and facilitate a quicker recovery.
Security Awareness Training: Educate yourself and your family members about common cyber threats, such as phishing, malware, and social engineering attacks. Stay informed about the latest scams and security best practices to avoid falling victim.
Monitor Your Online Presence: Regularly check your online accounts and credit reports for any signs of unauthorized activity. Set up alerts and notifications to stay informed about potential breaches or unusual transactions.
Report Suspicious Activity: If you suspect a security breach or encounter any suspicious activity, report it immediately to the relevant authorities or service providers. Prompt action can help mitigate the damage and prevent further exploitation.
Conclusion
The Lauren Compton leak serves as a stark reminder of the fragile nature of online privacy and the constant evolution of cyber threats. As we navigate the digital landscape, it is crucial to remain vigilant, proactive, and well-informed about the potential risks and preventive measures.
By understanding the methods employed in this breach and the broader implications, individuals, businesses, and governments can work together to create a safer digital environment. While complete security may be an elusive goal, continuous adaptation and a proactive approach can significantly reduce the likelihood and impact of such incidents.
Let the Lauren Compton leak be a catalyst for positive change, inspiring a renewed commitment to digital security and privacy for all.
How can individuals protect their personal data online?
+Individuals can safeguard their personal data by employing strong passwords, using two-factor authentication, regularly updating software, and being cautious about the information they share online. Additionally, privacy settings should be reviewed and adjusted to limit public access to personal details.
What steps should businesses take to enhance their security measures?
+Businesses should implement robust access controls, regularly update security protocols, and educate their employees about potential threats. Incident response planning is crucial, including regular security audits and the establishment of a dedicated cybersecurity team.
How can governments address digital privacy concerns?
+Governments can play a vital role by enacting and enforcing comprehensive data protection regulations. This includes implementing strict data breach notification requirements, imposing penalties for non-compliance, and providing resources to educate individuals about their digital rights and privacy.
What are some practical steps individuals can take to secure their digital presence?
+Individuals can secure their digital presence by using strong passwords and two-factor authentication, keeping software updated, being mindful of privacy settings, and opting for secure communication channels. Regular data backups and security awareness training are also crucial.