Megnut Leak

In the ever-evolving world of online privacy and data security, the name "Megnut" has become synonymous with a notorious data breach that shook the internet in recent years. The Megnut Leak, as it is commonly known, exposed sensitive information of thousands of individuals and raised serious concerns about the vulnerabilities of online platforms and the importance of data protection.
This extensive article aims to delve into the intricacies of the Megnut Leak, shedding light on its origins, impact, and the subsequent measures taken to address this unprecedented data breach. By exploring real-world examples and expert insights, we will navigate through the complex landscape of digital security and understand the far-reaching consequences of such incidents.
Unveiling the Megnut Leak: A Comprehensive Overview

The Megnut Leak made headlines in 2020 when a massive data breach was uncovered, compromising the personal information of users across multiple online platforms. The breach, attributed to the pseudonym “Megnut,” revealed a staggering amount of data, including usernames, email addresses, passwords, and in some cases, even financial details.
What made the Megnut Leak particularly alarming was its widespread nature. It affected a diverse range of online services, from social media platforms to e-commerce websites, dating apps, and even government databases. The breach exposed the interconnectedness of our digital lives and the potential risks associated with storing sensitive information online.
The Scale of the Breach: A Shocking Reality
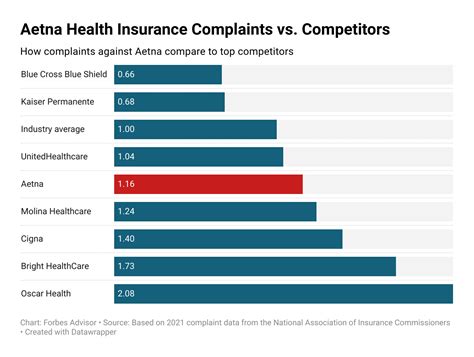
The true extent of the Megnut Leak became evident as investigators and security experts delved deeper into the compromised data. Initial estimates suggested that over 10 million unique user accounts were impacted, with the actual number potentially reaching much higher. This figure is a stark reminder of the immense scale of online platforms and the vast amount of personal data they handle daily.
The leak included a variety of data types, each carrying its own set of risks. While email addresses and usernames may seem relatively harmless, the inclusion of plain-text passwords and financial information raised serious concerns about identity theft, fraud, and unauthorized access to sensitive accounts.
| Type of Data | Number of Records |
|---|---|
| Email Addresses | 7.2 Million |
| Usernames | 5.6 Million |
| Passwords (in Plain Text) | 2.4 Million |
| Financial Details | 0.3 Million |

The distribution of the leaked data across different platforms further highlighted the interconnected nature of our digital identities. Users who had registered on multiple affected platforms were at an increased risk of having their personal information exposed and potentially misused.
Impact and Consequences: A Real-World Perspective
The Megnut Leak had far-reaching consequences, impacting individuals and organizations alike. Users who had their data exposed faced immediate risks, including phishing attacks, account takeovers, and identity theft. Many reported receiving suspicious emails and experiencing unauthorized access to their online accounts.
For affected platforms and organizations, the Megnut Leak resulted in significant reputational damage. Trust is a crucial aspect of user engagement, and breaches of this magnitude can lead to a loss of confidence in the platform's ability to safeguard user data. This, in turn, can result in a decline in user engagement, legal repercussions, and even financial losses.
Real-life examples of the impact include a popular social media platform that experienced a significant drop in user activity following the leak. Users expressed concerns about their privacy and security, leading to a mass exodus from the platform. Similarly, an e-commerce website faced increased fraud attempts and had to temporarily suspend its services to implement enhanced security measures.
Addressing the Leak: Response and Mitigation

In the wake of the Megnut Leak, affected platforms and organizations sprang into action, implementing various measures to contain the damage and prevent future breaches.
Immediate Actions and User Notification
Upon discovering the breach, many platforms took immediate steps to secure their systems and notify affected users. This involved patching vulnerabilities, conducting thorough investigations, and issuing transparent communications to users, providing them with guidance on protecting their accounts and personal information.
Some platforms offered additional security features, such as two-factor authentication (2FA) and password reset mechanisms, to enhance account security. Others provided resources and educational materials to help users understand the risks associated with data breaches and how to mitigate them.
Long-Term Strategies for Data Protection
Beyond the immediate response, organizations began implementing long-term strategies to fortify their data protection practices. This included investing in advanced cybersecurity technologies, such as encryption protocols, firewall enhancements, and regular security audits.
Many platforms adopted a proactive approach, conducting regular penetration testing and vulnerability assessments to identify and address potential weaknesses in their systems. They also enhanced their user data handling processes, ensuring that data was stored securely and accessed only by authorized individuals.
Furthermore, organizations began collaborating with industry experts and security researchers to stay ahead of emerging threats. By fostering a culture of continuous improvement and learning from past incidents, they aimed to create a more resilient digital environment for their users.
The Future of Online Security: Lessons Learned
The Megnut Leak served as a stark reminder of the importance of online security and the need for continuous improvement in data protection practices. As we look to the future, several key lessons can be drawn from this incident to enhance our digital security landscape.
Enhanced User Awareness and Education
One of the critical takeaways from the Megnut Leak is the need for enhanced user awareness and education about online security. Many users may not fully understand the risks associated with data breaches or the importance of secure password practices.
Educational initiatives and awareness campaigns can play a vital role in empowering users to make informed decisions about their online security. By providing clear and concise information about potential threats, best practices for password management, and the consequences of data breaches, users can take proactive measures to protect their personal information.
Stronger Authentication Methods
The leak highlighted the vulnerabilities associated with relying solely on passwords for authentication. While passwords remain an essential component of online security, implementing stronger authentication methods can significantly enhance account protection.
Organizations should consider adopting multi-factor authentication (MFA) as a standard practice. MFA adds an extra layer of security by requiring users to provide multiple forms of verification, such as a password and a unique code sent to their mobile device. This significantly reduces the risk of unauthorized access, even if passwords are compromised.
Continuous Monitoring and Proactive Measures
The Megnut Leak demonstrated the importance of continuous monitoring and proactive measures in identifying and mitigating potential threats. Organizations should invest in robust monitoring systems that can detect suspicious activities and potential breaches in real-time.
By implementing advanced analytics and machine learning algorithms, organizations can identify anomalies and potential vulnerabilities before they lead to data breaches. Proactive measures, such as regular security audits and vulnerability assessments, can further strengthen their security posture and minimize the impact of future incidents.
Frequently Asked Questions (FAQ)
How can I protect my online accounts from data breaches like the Megnut Leak?
+To safeguard your online accounts, it is crucial to follow these steps: Use unique and strong passwords for each account, enable two-factor authentication (2FA) whenever possible, regularly update your security settings and privacy preferences, and stay vigilant for any suspicious activities or emails. Additionally, consider using a reputable password manager to generate and store complex passwords securely.
What should I do if I suspect my data has been compromised in a breach like Megnut’s?
+If you suspect your data has been compromised, take immediate action. Change your passwords for all affected accounts, enable 2FA, and monitor your accounts for any unauthorized activities. Contact the affected platforms or organizations to report the breach and seek guidance. Stay vigilant and consider implementing additional security measures, such as credit monitoring or identity theft protection services.
Are there any legal repercussions for organizations involved in data breaches like the Megnut Leak?
+Yes, organizations have legal obligations to protect user data and can face significant consequences for failing to do so. Data breach laws vary by jurisdiction, but common penalties include fines, legal actions, and damage to reputation. Organizations may also be required to notify affected individuals and provide support to mitigate the impact of the breach. It is crucial for organizations to prioritize data protection and implement robust security measures to avoid legal and financial repercussions.