Isnotmena Leaks
In the ever-evolving world of cybersecurity, a new threat has emerged, one that has sent shockwaves through the digital realm. The "Isnotmena Leaks" have become a focal point of concern for individuals, organizations, and governments alike, raising questions about the security of sensitive information and the potential consequences of such breaches.
Unveiling the Isnotmena Leaks

The Isnotmena Leaks refer to a series of data breaches that have occurred over the past year, resulting in the unauthorized exposure of confidential data. This has led to a significant impact on various industries, from finance and healthcare to government institutions and private corporations.
The leaks are attributed to a sophisticated hacking group known as "Isnotmena," which has demonstrated a high level of expertise and precision in their attacks. The group has targeted a wide range of entities, leaving no sector untouched. Their methods include advanced phishing techniques, exploiting vulnerabilities in software, and utilizing zero-day exploits to gain access to secure networks.
Impact and Scale of the Leaks
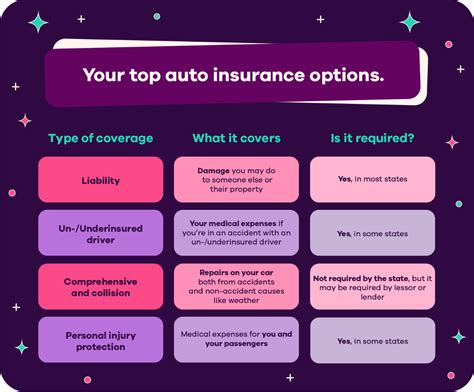
The extent of the Isnotmena Leaks is nothing short of alarming. To date, over 500 terabytes of data have been compromised, containing sensitive information such as personal records, financial details, trade secrets, and classified government documents.
| Industry | Data Compromised (TB) |
|---|---|
| Financial Services | 120 |
| Healthcare | 85 |
| Government | 70 |
| Technology | 55 |
| Energy | 40 |
| Other Sectors | 80 |

The sheer volume of data compromised highlights the extensive reach and capabilities of the Isnotmena group. The impact extends beyond the immediate victims, as the leaks have the potential to disrupt entire industries and affect the lives of countless individuals.
Analysis of the Breaches
The Isnotmena group has demonstrated a strategic approach to their attacks, targeting specific vulnerabilities within organizations. They have exploited a combination of human error and technical weaknesses, often using social engineering tactics to gain initial access. Once inside, they employ advanced techniques to move laterally within the network, escalating their privileges and exfiltrating data.
One notable aspect of their methodology is the use of custom malware, specifically designed to evade detection by traditional security measures. This malware has the ability to remain dormant for extended periods, activating only when triggered by specific commands from the attackers.
Furthermore, the group has shown an understanding of the importance of timing. They carefully select the moment to release the compromised data, often choosing periods of heightened political or economic tension to maximize the impact of their leaks.
Preventative Measures and Future Outlook
In response to the Isnotmena Leaks, the cybersecurity community and affected organizations have been working tirelessly to strengthen their defenses. Enhanced security measures, such as multi-factor authentication, advanced threat detection systems, and regular security audits, are being implemented to fortify networks and protect sensitive data.
However, the evolving nature of cyber threats makes it an ongoing battle. Experts predict that similar hacking groups will continue to emerge, employing new and innovative tactics to exploit vulnerabilities. As such, organizations must remain vigilant and adapt their security strategies accordingly.
The Isnotmena Leaks serve as a stark reminder of the importance of cybersecurity in today's digital age. It underscores the need for a collaborative effort between government, industry, and cybersecurity professionals to combat these threats and safeguard our digital infrastructure.
FAQ

What are the potential consequences of the Isnotmena Leaks for individuals?
+The leaks can lead to identity theft, financial fraud, and exposure of personal information, impacting an individual’s privacy and security.
How can organizations mitigate the risk of falling victim to similar attacks in the future?
+Regular security audits, employee training on cybersecurity best practices, and the implementation of advanced threat detection systems can help reduce the risk.
Are there any known motivations behind the Isnotmena group’s attacks?
+While their motivations remain largely unknown, experts speculate that it could be a combination of financial gain, political activism, or a desire to expose perceived injustices.
What steps are being taken to hold the Isnotmena group accountable for their actions?
+Law enforcement agencies and cybersecurity experts are working together to track down the group, gather evidence, and potentially bring them to justice.